Dissecting Mikrotiks Mac-Telnet packets
I was searching on the Internet if there were any MAC-Telnet clients for linux/posix, since using terminal.exe in wine is problematic sometimes, as wine gives it access to only one of the NICs in your computer.
I didn’t find any clients, but I found this nice reverse engineering of the protocol, which interested me, because I’ve always wondered how it was made, just not enough to check myself. But this guy has done his homework and then some in reverse engineering of Mikrotiks protocol.
You can find his page here: http://www.omniflux.com/devel/
This gave me an Idea to create a MAC-Telnet client myself, and I started some testing with perl to check if I was able to send the correct packets to my mikrotik router. At first you might think; thats easy! All packets via the mac-telnet protocol uses UDP packets, with both source- and destintation port: 20561.
But you can’t send these packets with your normal socket wrapper library, because you need to set the mac-addresses in the network frame to something other than the source/destination IPs corresponding ARP entry. To go into details: When you send Mac-Telnet packets as a client, you need to send your packets going from your ip to ip 255.255.255.255, but with the router you want to telnet as the destination mac address in the ethernet frame. (even though the ip is set to 255.255.255.255).
To test this in perl, I used Net::RawIP from CPAN, which worked just like I wanted to. The only problem is that you need to have root access to be able to do raw packets.
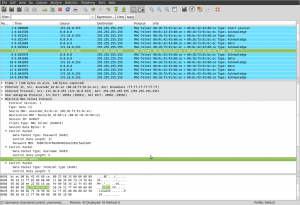
Anyways, I looked at the packet I sent with my test script, and the response from the RouterBoard with Wireshark. Even though I got it to work, I felt I was having problems reading the packets very easily: Reading omniflux’s protocol description, and then looking at the hex dump of the packet. So I decided to make a dissector plugin for Wireshark (ethereal), so I could debug the packets easier.
Here is the finished source code for the Wireshark plugin (GPLv2): mactelnet.diff
Just patch this in from the root of the wireshark sources.
[Update: It is now added in the wireshark svn trunk]
[…] I wrote about a Wireshark plugin for dissecting Mac-Telnet packets. Now I have created an open source application for connecting to […]
October 1st, 2010 at 12:28[…] bloqueo a nivel de firewall (Capa 3) y nos encontremos en el mismo segmento.Este usuario realizó un estudio de los paquetes que se generaron en una conexión MAC-Telnet y a través de un plugin de Wireshark logró entender […]
October 12th, 2010 at 00:25Can you tell me how use the plugins (mactelnet.diff)?
Thanks
August 13th, 2012 at 18:28Just install the latest Wireshark. The patch is included there.
August 27th, 2012 at 11:26